Be Aware of Amazon Phishing Attempts This Holiday Season
This time of year, 80% of holiday shoppers will use Amazon for some of their gift purchases (according to CPC Strategy).
A collection of articles that will keep your South Carolina business secure, productive, and profitable. Our blog covers a wide range of topics, from cybersecurity to productivity tips, designed to help you navigate today's digital landscape with confidence.
We share strategies for optimizing your IT support, protecting your valuable data, and leveraging Microsoft 365 security features effectively. Stay informed about the latest trends and best practices in cybersecurity, budgeting, and running a business.
This time of year, 80% of holiday shoppers will use Amazon for some of their gift purchases (according to CPC Strategy).
Data Security Methods That Are Effective for SMBs to Protect Themselves Against Today’s Risks.
There is no such thing as completely bulletproof security. Every software has vulnerabilities. However, there is one security tool that has been found to block

DEF CON is the world’s largest underground hacking conference. It’s been running since 1992 and is always a wealth of information about cybersecurity vulnerabilities.
His name is Evaldas Rimasauskas and he’s a 50-year old man from Lithuania. Last Wednesday, he pled guilty to a phishing scam that fooled tech
Baltimore — as in the entire city, has been dealing with the ramifications of a cyberattack that froze thousands of computers, brought emails to a

It’s a common traveling scenario: you get off the plane and walk into the airport. With time to kill before your connecting flight, you think
When it comes to the relentless amount of cyberattacks going on right now, the goal for any business is to minimize risk and avoid being
It’s scary that large data breaches are becoming a weekly occurence. A recent report by Malwarebytes found that cyber threats are up 235% year-over-year!
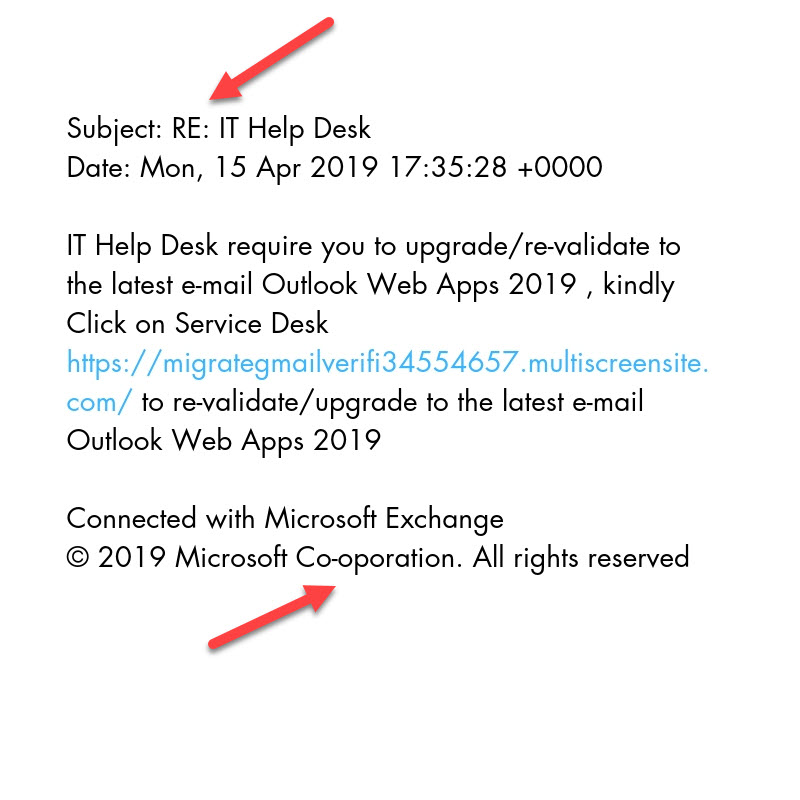
We always see an increase in phishing attacks right before tax season and into travel-heavy summer. This year is no different.