We always see an increase in phishing attacks right before tax season and into travel-heavy summer. This year is no different.
Bad guys are looking for two things when they create these elaborate spoofs and phishing attempts:
1. To catch a person off-guard when they might be stressed or in a more gullible mood.
2. To gain credentials or account access quickly in order to get a payoff.
Imperva, an IT security company, identified that 35% of all attacks happen between 9am-12pm. Also 68% of breached accounts had never been breached before.
Here are 3 current Office 365 attacks to be aware of.
We’ve witnessed these attacks appearing in user’s environments recently. While Microsoft 365’s multi-layered filtering solution will catch a lot of these, there will always be some that will slip through the cracks.
You must be educated, careful and aware…
Don’t fall for this spoofed Microsoft email telling you to update your password.
Check the source, check where the link is actually going. ATP safe links can prevent clicking through to a malicious site.
You’ll notice that the sender’s email looks suspicious under close examination, “microsfrtfonline.” A lot of the text and logos in this email are real (copied from actual Microsoft correspondence) however, the “portal” link is hiding the malicious content. If you hover over this link (be careful not to click) you’d see that it re-directs to a non-Microsoft site.
Or this phishing email pretending to be from your IT support provider
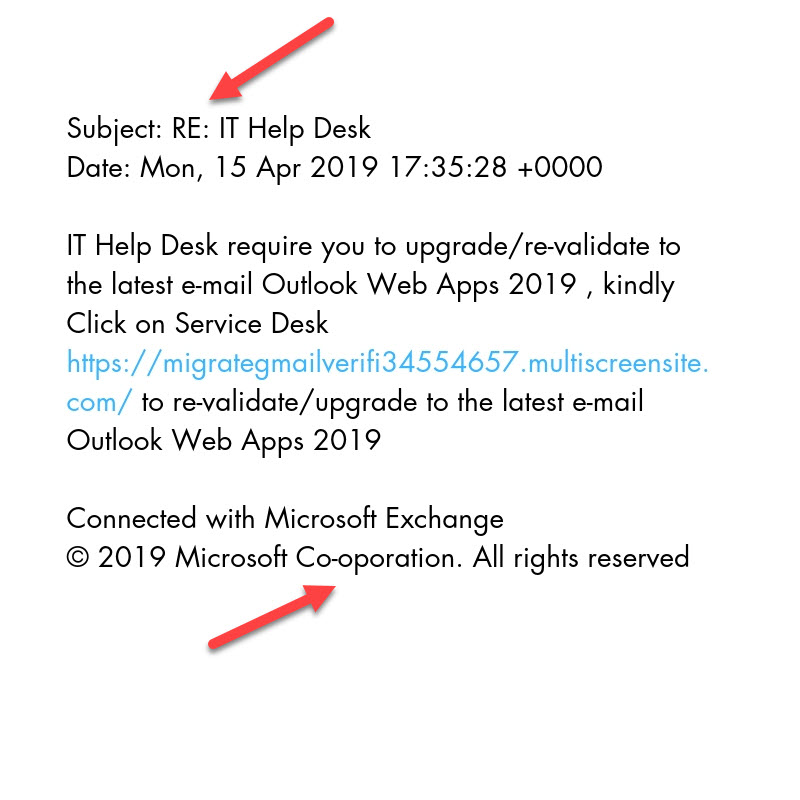
This one is less sophisticated than the first example, but still effective as a phishing attack. Again, this is a real email that was circulating just a few weeks ago.
The “RE: IT Help Desk” Subject line lends this message its spoofed credibility. You can imagine if you had recently opened a ticket with your IT service provider how you would be compelled to open this.
Spelling errors and typos are often giveaway’s that emails like this might not be legit “Co-oporation” is the suspicious error here.
In this case, the best thing to do is to check with the sender to see if they actually did send you an email before you click the link.
Watch out for this attack that mimics an email return path to steal your credentials
Some clever phishing attacks anticipate user actions and spoof messages that they may normally receive.
This message presumes to alert the user to undelivered email messages they may have sent. This message includes to traits that phishing emails often have:
1. Urgency. The “Action Required” in red text compells the user to take action soon before fully thinking things through. While this is a real component of a non-delivery receipt, you need to verify any message’s legitimacy before acting.
2. The easy to click “Send Again” button. A Phishing email must make it extremely easy for the target to click the malicious link. You’ve been told that action is required and now they are providing the quick fix. A real non-delivery receipt does not include this option.
Again, a lot of items in this email are legit, but the message hopes that you won’t actually take the time to check your outbox to see if recent messages bounced.
It is always advisable to research what a message like this is telling you before taking the requested action.
Beware of spoofed log-in pages
Guess what happens when you click that “Send Again” button in the last example? It goes to this spoofed Microsoft log-in page to steal your password.
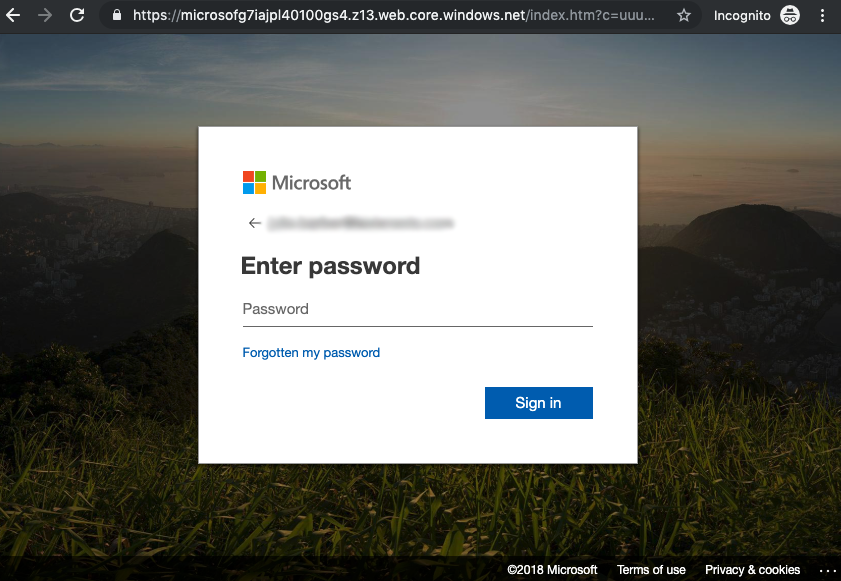
Phishing attacks are getting trickier all the time. The spoofing is getting better with multiple steps and re-directs looking more like the real thing. Even header and sender info can be spoofed.
New forms of these attacks appear every day. Make sure you take precautious to stay safe:
1. Don’t click links unless you can verify the sender. Hovering over a link will sometimes reveal its true nature.
2. Look for typos and language that seems out of character for the real message that is being spoofed.
3. Use multi-factor authentication (MFA) on all devices to further protect your identity.
4. Have an expert cybersecurity team you can call when suspicious activity occurs.
PTG offers a complete “security suite” for your business, offering the latest in real-time email monitoring, cybersecurity, MFA, customized log-in pages and A.I. enhanced virus protection. If you need to protect your business from a costly breach, contact us today.