The reality of the world post-COVID is that everything is different than it was before, from personal connections to business meetings and well beyond. To cope with this new norm, many businesses are taking a hybrid work approach, pairing in-person and remote work to fit the needs of their workforce. And over half of employees (55%, according to one study) would prefer to be remote at least three days a week once pandemic concerns die down.
As hybrid offices become more common, the attack surface for cyber threats continues to expand. Microsoft and CISO have identified six pillars – each of which is interconnected by automated enforcement of security policy, correlation of signal and security automation, and orchestration – for securing your hybrid workforce:
In this blog, we will explain each pillar to equip you with the knowledge you need to help protect your company’s data.
{{cta(’45d7570a-94d2-47ec-8acf-795f56036af6′)}}
Identities
Identities are anything that represents people, services, or IoT (Internet of Things- think smart light bulbs or your Apple TV) devices. As companies adjust their day-to-day toward a more hybrid setup, Microsoft has seen more than a 220% increase in new multifactor authentication (MFA) usage in the last 18 months. That is, and this is only a guess, due entirely to this blog on making MFA more convenient, or maybe this one on 2FA vs. MFA.
Regardless of the additional security measures, hackers remain undaunted. In Azure Active Directory (Azure AD), Microsoft has observed around 61 million password attacks daily so far in 2021. While strong authentication programs can protect against just about every kind of identity attack, passwordless multifactor authentication is a better option as the most usable and secure authentication experience.
Legacy protocols, such as IMAP, SMTP, POP, and MAPI are another major source of compromise. Because of their age, these protocols do not support updated multifactor authentication programs. Because these are so easy to exploit, 99% of password spray and 97% of credential-stuffing attacks exploit legacy authentication (which lacks multifactor authentication).
Endpoints
After an identity is securely granted access to an account, data begins to flow between different endpoints on the digital spectrum, from IoT devices to smartphones, BYOD to partner-managed devices, and on-premises workloads to cloud-hosted servers, all creating a massive attack surface for anyone looking with nefarious intent.
Zero Trust Architecture, as defined by Microsoft –
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.”
Every access request is fully authenticated, authorized, and encrypted before granting access. Microsegmentation and least privileged access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real-time.
Does anyone else picture hacker Gargamel rubbing his hands together victoriously over mounds of sad, anthropomorphized data-Smurfs? Well, if you didn’t before, now you do. ~You’re welcome.
Anyway, with a zero-trust model, businesses opting for a hybrid office model can keep provisioning costs down while avoiding additional hardware purchases for work-from-home employees. For example, your admin can grant access to verified and compliant devices ONLY, restricting access from any personal devices rooted or jailbroken. This prevents your organization’s applications from exposure to vulnerabilities.
Applications
Current modern applications and services require users to be given access or authenticated in another way prior to gaining access. That said, many of these apps use VPNs and other network firewalls to prevent unsavory types from charging through the digital gate. But these traditional architectures built for legacy apps were constructed for lateral connectivity (CorpNet) rather than micro-segmentation.
Additionally, these architectures violate the fundamental principle of least privilege access, making them significantly more vulnerable to lateral movement across the network by anyone looking to gain access to your information.
To modernize your applications, use one of these three solutions from Microsoft:
- Move to a serverless, cloud-based SaaS or PaaS-based service.
- Utilize application tiers that only expose minimal least-privileged-access endpoints.
- Add an internet hybrid endpoint, like a reverse proxy or other secure-access service edge system (SASE).
Network
Azure Firewall blocks millions of attempted digital break-ins every single day. The attackers are most commonly using malware, phishing, web applications, and mobile malware in their attempts but in July, there was a dubious rise in the use of “coin-miners”, malware that mines cryptocurrency from networks.
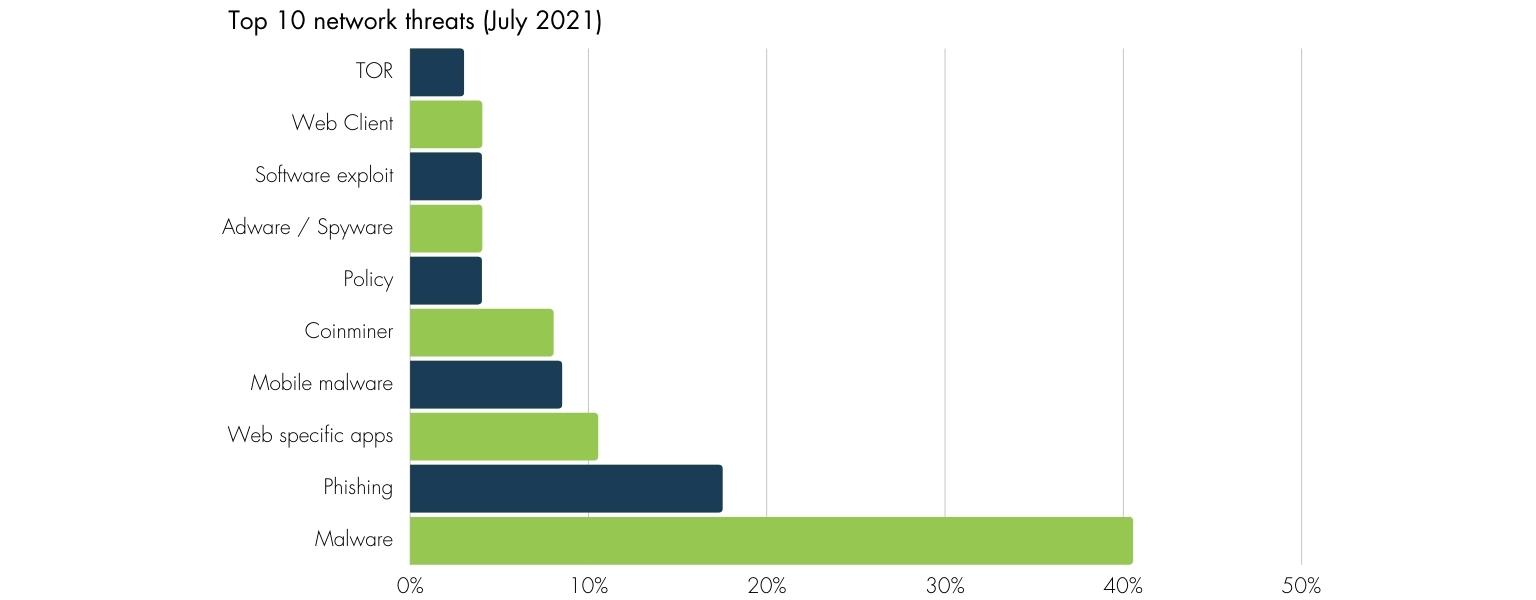
Figure sourced from Microsoft
The attack protocols leveraged most often were HTTP, TCP, and DNS, since they are all open to the internet. Utilizing a Zero Trust approach to securing your network means you consider your network constantly under attack. This means you should be prepared with a segmented layout that minimizes the blast radius.
Distributed Denial of Service (DDoS) attacks on internet-facing endpoints have risen significantly since the beginning of the year. Compared to the end of last year, attacks requiring rebuffing rose 25% over the first six months this year, and the average attack bandwidth per-public IP increased by 30 percent.
Azure DDoS Protection mitigated 1,200 – 1,400 unique DDoS attacks every day over those same six months. The most commonly attacked regions are Europe, Asia, and the USA thanks to their heavy concentration of tech-forward industries like financial services and gaming, and over 96% of those attacks were considered short or lasting fewer than four hours.
Infrastructure
Infrastructure represents a critical threat vector, whether on-premises, cloud-based, virtual machines (VMs), containers, or micro-services. With the move to the cloud enabling a significantly more secure hybrid workforce, organizations in every corner of the market are increasing their dependency on cloud solutions. This dependence means more effective threat protection is required, including mitigation strategies and efficient tools that manage access to your networks.
Azure Defender operations assuming data-centric services, like cloud storage accounts and big data analytics platforms, are a part of the security perimeter, prioritizing and mitigation of threats. Microsoft has produced a threat matrix for storage to help businesses identify holes in their digital defenses. The expectation is that the matrix will evolve as more threats are discovered, and cloud infrastructures will constantly progress toward securing their services.
Data
Upwork estimates say 26.7% of the workforce will be fully remote by the summer of 2022, and their estimated number of future full-time hybrid workers is DOUBLE the figure pre-COVID. With this meteoric rise of a new kind of far-flung workforce, it’s critical that data remain protected even if it leaves the devices, apps, infrastructure, and networks your organization controls.
Organizations that can effectively manage the lifecycle and flow of their secure data as part of their day-to-day operations make it significantly easier for data security and compliance teams to reduce exposure and manage the risk involved. This means reconsidering how your organization conducts business with its sensitive data to ensure proper storage, access, flow, and lifecycle.
Conclusion
As we look past the pandemic to a time when workforces and budgets finally rebound, zero trust will become the biggest area of investment for cybersecurity. Hybrid work is the new normal, and organizations need to remain constantly vigilant regarding how to defend themselves against a constantly evolving threat landscape.
For more information on topics like hybrid work security, sign up for PTG Tech Talk and follow us on LinkedIn, Facebook, and Twitter!
