First, the FBI recently reported business email compromise attacks were up 65% from July 2019 through December 2021 and totaled $43 Billion dollars – that’s BILLION with a B – in reported losses from June 2016 through July 2019.
Additionally, if you and your team do business on the internet, you are at risk. Okay, that sounds click-baity, too, but it’s absolutely true. We’ve said it over and over. There are plenty of proactive options to build a strong strategy.
So that’s the headline in a nutshell. But if we wanted to just pass along Twitter-length-approved paragraphs, we’d probably do that on Twitter instead, right? So let’s take this opportunity to sit back and read like, I dunno, around 1000 words about one of the most dangerous threats to your business and discuss:
- What Business Email Compromise actually is
- How BEC is so effective at tormenting businesses
- What businesses can do to prevent compromise
What is Business Email Compromise?
Business Email Compromise, or BEC for short, is a form of social engineering which is an attack where someone uses human interaction and some form of social skills to compromise crucial info regarding a business and its computer systems. Attackers may seem unassuming and respectable through their interactions, nearly always taking a false identity that disarms the target.
To attempt to capture specific answers and/or seduce – yeah we said it – clicks where they aren’t deserved, often legitimate senders’ addresses can be spoofed or written similarly enough to pass as identical. When sending out mass attempts, generic greetings, and signatures, which often don’t match the content of the email, are included with spoofed hyperlinks and websites.
Finally, many use the dreaded malware. Malicious software can be instructed to infiltrate target networks to gain access to email threads about financial topics. That information is then used to time specifically spoofed requests, or send messages to accountants to create a mirage. Malware is also an easier way for criminals to gain access to data like passwords and financial account information.
Why is BEC so effective?
According to the FBI’s IC3 2021 Internet Crime Report, BEC scams were the cybercrime with the highest reported total victim losses last year. However they choose to gain access, the overarching goal is always to break into the network to… you know… *blank* stuff up… though the specific end game is often different depending on the victim, attacker, and situation. It’s impossible to say why businesses are chosen; often there are hundreds or thousands in the crosshairs at once while only a few fall victim in the end.
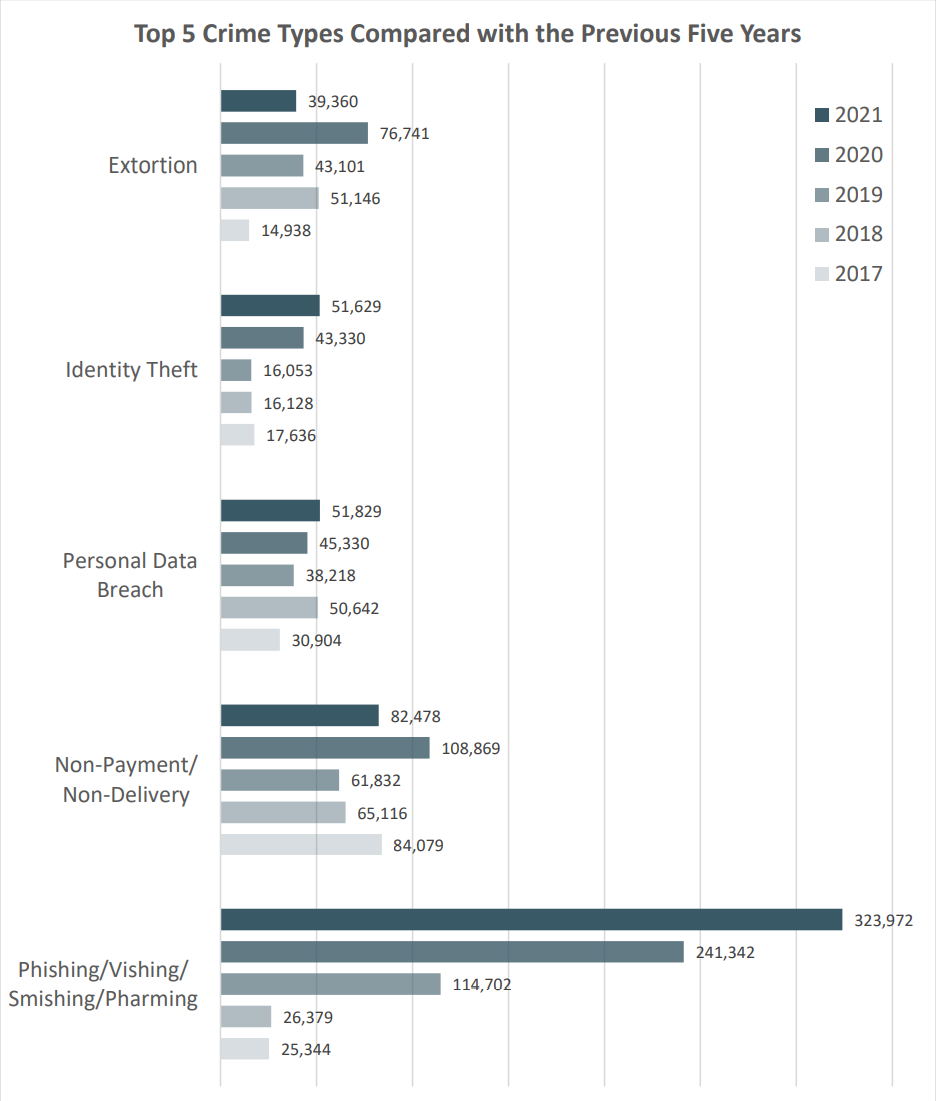
Source: 2021 IC3 Report
Essentially, BEC is effective because it uses the social engineering and specifically timed messaging mentioned before to hide what’s going on, the same way a magician uses smoke and mirrors to redirect the eye. Though many of these bad actors would fail to fool Penn & Teller on their television show, the FBI has revealed the steps these criminals are using, breaking the magician’s code.
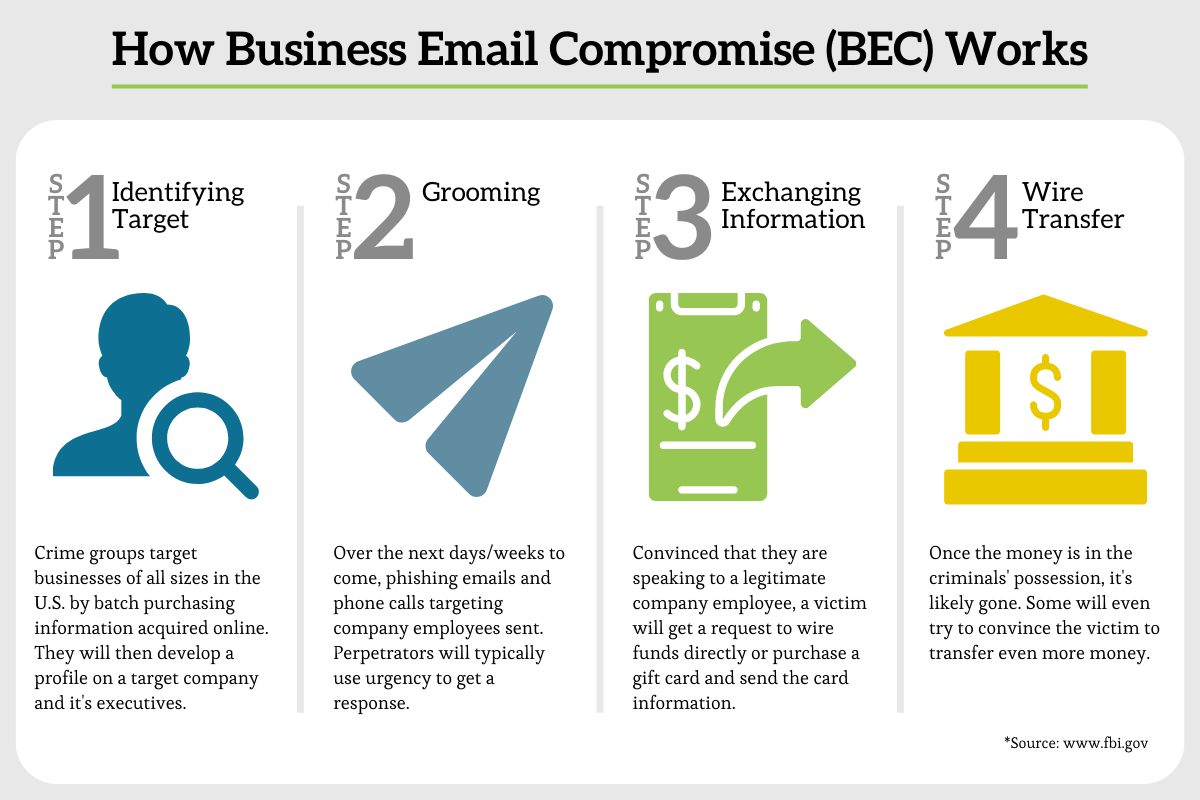
Okay, so it’s not that magical of a process. In fact, it’s pretty straightforward. But that’s what makes it so effective. It’s simple.
We’re all so busy we hardly have time to stop and check every single character of an email. Many managers at sprawling organizations have no way of knowing what new hire started states, countries, or even hemispheres away. We click links without checking them all the time – just ask my dad.
What can be done to stay safe?
So at this point, you have to be asking yourself the question from the title of this section. Or you’re skimming around and are confused about how we got here – scroll back up, Derek.
First and foremost, literally, if you suspect or detect a breach, you must contact your financial institution and IT and report the trouble immediately. Right away. (Is that clear enough?) After that is taken care of, you will be armed with the information necessary to contact your local FBI field office to report the crime, where you may be directed to file a second report with the Internet Crime Complaint Center (IC3).
Additionally, here are some other ways to proactively protect yourself and your business:
- Don’t overshare on social media. For literally anyone in your organization, posting information like pet’s names, past schools, family members, and especially birthdays can unknowingly give a scammer everything they need to guess or reset a password. This is the most straightforward example of current social engineering.
- Don’t click unsolicited emails or text messages. If an email or other message comes through asking for privileged info, look up the person separately – and professionally of course – and call the company to ask them to verify the request. Trust but verify, or better yet, never trust and always verify.
- Check every correspondence before engaging. Carefully look at the email address from your sender, hover over the URL, and confirm spelling used. As mentioned before, scammers often utilize slight differences to trick your eye to gain your trust.
- Watch what you download. Ahem, Pam. Never open an email attachment or download a file from someone you don’t know, and that usually goes 100% for anyone outside of your network. Be wary of email attachments forwarded to you, even if they could be funny.
- Set up multi-factor authentication. Seriously, how have you not set up your MFA?
- Verify payment and purchase requests. It may not always be possible to verify everything in person, but often calling the person making a request can be the difference between a breach and security. Verify any change in account numbers or regular payment procedures directly with the person making the request.
- Remember, slow and steady. Everyone has their deadlines, but be especially wary if the person making requests is pressing you to act quickly. Take your time, check every box you can, and make the right decision every time.
If you are ready to start protecting your business from cyber threats, click here
Conclusion
Let’s say this: We really, really hope this never becomes a problem for you. It seems like a huge pain in the butt, and we’re firm believers in working hard to prevent situations like this from ever occurring. The path toward safety is paved with potholes, especially in an increasingly digital workplace. With new technology comes new challenges, but the best news is that if you follow the guide to staying safe, it is very unlikely to affect you and your business.
To learn more about how to protect your business from the $43B scam of business email compromises, give us a call at (864) 552-1291 and we’ll help you evaluate capabilities and options. Also, sign up for PTG Tech Talk for bi-monthly tech news and consider following us on LinkedIn, Facebook, and Twitter!
