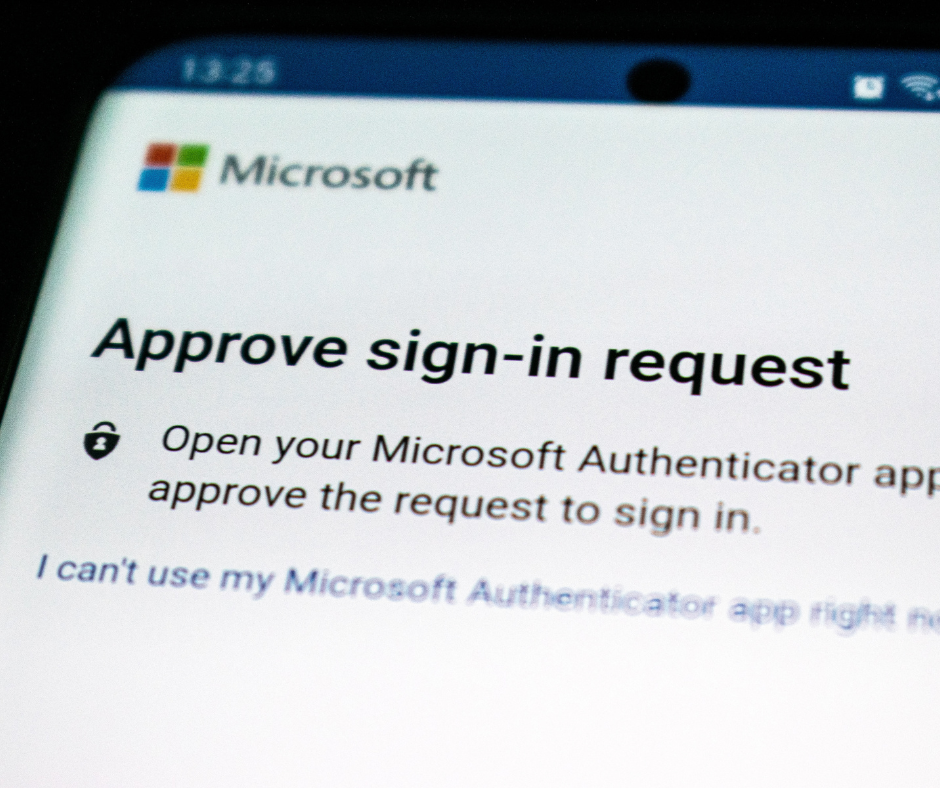
Back in October 2019 – you know, before it all changed – Microsoft beta-tested a new baseline security program with 30 million users. We let the mega-computers crunch all of those numbers but the result was astoundingly clear: Adding things like MFA and conditional access to accounts made a world of difference.
To be fair that isn’t exactly a surprising find. While it’s our job to care about how nefarious types are trying to get into your data, you’re likely busy thinking about the 99.9% of the rest of your business. Cakes, cookies, muffins, whatever kind of delicious baked goods you make. (And even if you don’t make baked goods, you should still keep reading..)
Even before this testing, Microsoft, and the industry as a whole, were well aware of the use of security features built-in, but not made mandatory, like multifactor authentication which prevents 99.9% of attempted breaches. So rather than let users languish after breaches that could have been presented by bare-minimum security standards being enabled, Microsoft has now created an all-new baseline security default that’s already protecting 30 million organizations.
In this blog, we’re going to look at what exactly Microsoft’s new baseline security defaults are and the details you need to know to keep your business safe.
Need to Know: Microsoft Baseline Security Defaults
As we were saying, in October 2019, new users were added to the Microsoft 365 platform with a new kind of “baseline security” in place regardless of license. This means that, as accounts were created, the minimum allowable security features were brought to a new level with defaulted settings for multifactor authentication and identity protection.
With over 30 million organizations protected by these automatic security defaults, the entire group has experienced 80% less compromise than other program users. Microsoft also found most users simply left the security settings on, while others decided to add even more security with Conditional Access when they became ready.
As terms and three-letter acronyms (TLAs) get tossed around, it can get difficult to keep track of what everything means. We wanted to define some common terms so that we’re all on the same page:
Multifactor Authentication
One of the most important tools to thwart unwanted attempts on your system, multifactor authentication adds an additional layer to your security, like combining a PIN and texted passcode with a biometric layer like a facial scan on a personal device.
This additional factor – knowledge, possession, inherence, or context… go read the blog if that’s not ringing a bell – creates a nearly impassable barricade between the hacker and information. By automatically setting MFA as the default for your Microsoft account, the baseline security is putting you in full control of all security, especially when an MFA hardware cryptographic device is used as recommended by NIST for AAL 3.
More about MFA: Making MFA More Convenient for your Business
Identity Protection
Another key addition to Microsoft’s baseline security, Azure Active Directory Identity Governance allows your organization to balance the need for security and employee productivity with the right processes and visibility for each user. The program uses entitlement management, access reviews, privileged identity management, and terms-of-use policies to make sure only the right people always have the right access to the right resources.
This program also aids in increasing productivity by streamlining access to apps, groups, and Microsoft Teams in one package. Users can be easily configured as approvers without involving administrators or additional time from upper management.
Conditional Access
This may seem complicated but at its core, nothing could be simpler. Conditional access is like a guard at the front of a private dance club door – only allowing the people in who are dressed for the part and have the right invitation to come inside.
Conditional access in a computer then is an automated, intelligent way of bringing together rules that enforce specific company policies in specific situations that arise for your team. It sets standards for if-then statements, specifically that if a user wants access to something they must prove their proper identity.
Conditional access is also often the catalyst for when MFA needs to be used. Policies created through conditional accessing can get super detailed for specific actions while still keeping everyone safe, like mandating MFA being used for anyone with an administrative role or other management tasks, granting access from specific locations, and even requiring in-house devices be used for access to work applications.
For more information on how to start protecting your business from cyber threats, click here
Will My Business Be Affected – and If So, When?
“When we look at hacked accounts, more than 99.9% don’t have MFA, making them vulnerable to password spray, phishing, and password reuse.” In a statement, Microsoft said, “Based on usage patterns, we’ll start [mandating MFA] with organizations that are a good fit for security defaults. Specifically, we will start with customers who aren’t using Conditional Access, haven’t used security defaults before, and aren’t actively using legacy authentication clients.”
Going on to mention global admins of eligible tenants being notified through email, the statement also says that, starting in late June, users will start to receive the following prompt during sign-in:
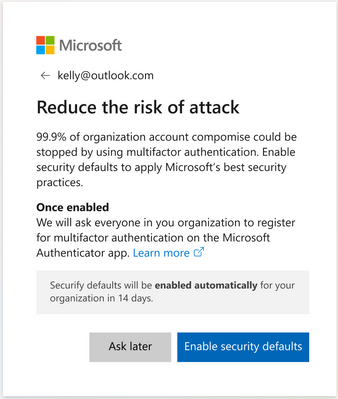
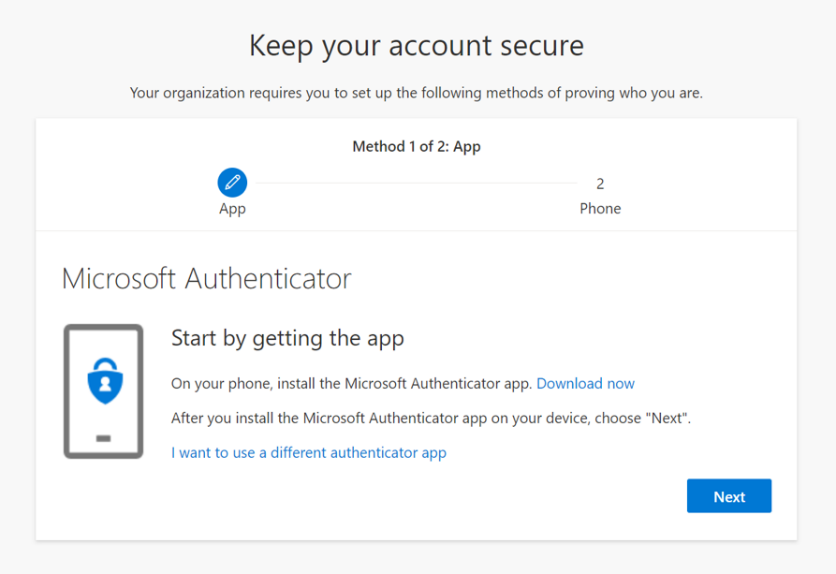
Global admins at these organizations can opt into security defaults right away or snooze for as many as 14 days – but we really don’t recommend waiting. After security defaults are enabled, the users on your site will be asked to register for MFA. They’ll be asked to register using the Microsoft Authenticator app, and Global administrators are additionally asked for a phone number. Users will have an additional 14 days to register for MFA. Here’s an example of what to look out for:

Conclusion
You may already have these security protocols enabled, and kudos for reading this all the way through if that’s the case, but likely you’re concerned about how security changes will impact your daily workflow and access to important info.
The good news? You’re not alone in your worry.
The better news? Microsoft has you covered with their new baseline security requirements.
The best news? You just read something interesting and helpful. Hopefully.
If you have further questions about the Microsoft security defaults, give us a call at (864) 552-1291 and we’ll help you evaluate capabilities and options. Also, sign up for PTG Tech Talk for bi-monthly tech news and consider following us on LinkedIn, Facebook, and Twitter!